A security vulnerability in popular dating app Tinder left users' exact locations open to interception for months.
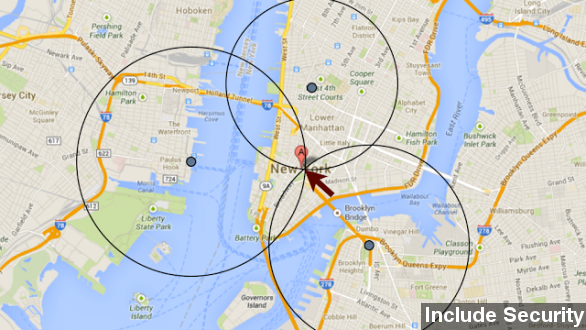
Research firm Include Security explains Tinder tracks the distance between nearby users, down to highly precise fractions of a mile. This value is rounded to the nearest whole mile on the public side of the app.
But Include Security says someone with a basic knowledge of programming could extract the full values straight from the application.
With multiple accounts, then, one could feasibly nail down another user's actual location, to an accuracy of 100 feet.
Include Security first told Tinder about the problem in October 2013, and Tinder reportedly patched the vulnerability before the new year — but the company never publicly acknowledged the risk.
In a statement to Bloomberg this week, a Tinder rep said "We did not respond to further inquiries about the specific security remedies and enhancements taken as we typically do not share the specifics of Tinder's security measures."
For what it’s worth, says The Verge, anyone using this hack would have had to know their target's current city and Tinder application ID number beforehand — "which meant that the hacker would likely have had to intercept their target's phone traffic in the past before putting the vulnerability to use."
But Tinder's no stranger to location troubles.
According to Include Security's report, the distance-tracking exploit was a direct result of another fix the company made in July of 2013, to prevent the app leaking exact latitude and longitude coordinates of its users.
It’s not clear exactly how or when Tinder secured its app against this most recent vulnerability. The last Include Security heard from Tinder was on February 7.